Continuously assess risks and refine response
plans to ensure your team has the best tools
and procedures.
At SecurityBoat, you get a unified platform that tracks vulnerabilities, prioritizes risks, and generates actionable reports, all in
real-time. We empower you with the tools to strengthen your organization’s defenses with ease and efficiency.


There is no such thing as a secure system! With the best minds in the security industry, we help complex organizations
protect their web applications, cloud, networks and mobile phones.
It is essential that the pentester and client interact prior to the engagement in order to conduct a successful penetration test. Due to pentesting's technological nature, this phase is vital. Just like any other IT project, it requires great planning.
 Meetings
Meetings
 Requirement's
Requirement's
 Scope
Scope
 Test Plan
Test Plan
It is a proactive strategy to evaluate cybersecurity threats using threat modelling. In this stage tests and procedures are developed to detect and respond to potential threats, which involve identifying potential threats. To do so, one has to understand how threats impact systems, classify threats, and apply the appropriate countermeasures.
 Classifying Threats
Classifying Threats
 Defining Assets
Defining Assets
 Identifying Threats
Identifying Threats
 Tighten Internal Controls
Tighten Internal Controls
This stage of offensive security consists of attack simulations, commonly referred to as penetration tests. It involves attacking networks, web applications, and software products to discover their vulnerabilities. During such a test, our pentesters attempt to gain access to critical infrastructure by attacking your company or solution.
 Automated Testing
Automated Testing
 Hacker Mindset
Hacker Mindset
 Limited Exploitation
Limited Exploitation
 Manual Testing
Manual Testing
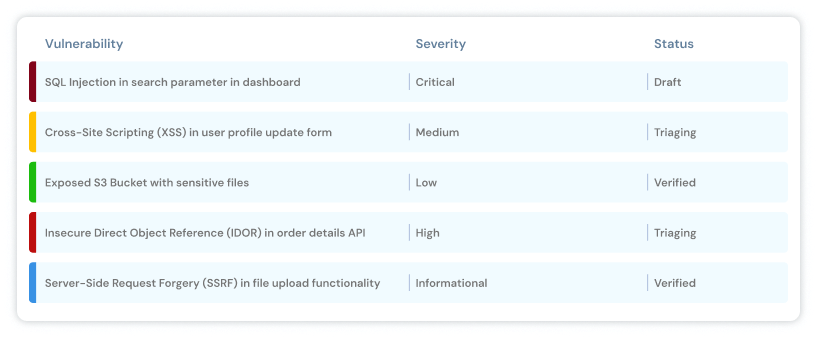
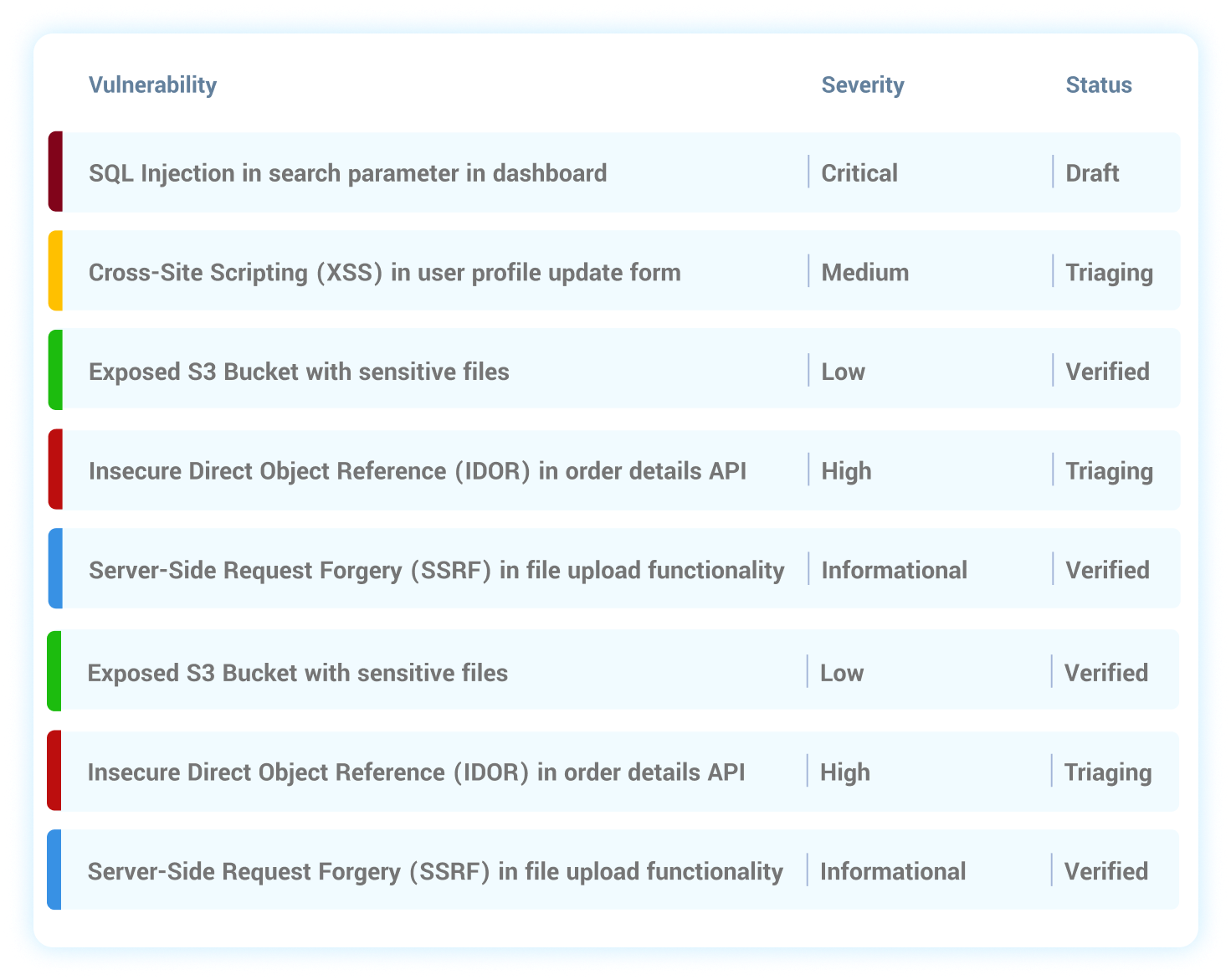
Once the assessment is complete, a detailed written report outlining each observed and or exploited vulnerabilities, along with the root cause analysis and categorization along with mitigation and confirmatory re-test certificate if the need arrives.
 Easy To Understand
Easy To Understand
 Graphical Representations
Graphical Representations
 Neat And Clean
Neat And Clean
 Quality Checked
Quality Checked
Every vulnerability has its own audit trail which contains remediation notes, to help track what remediation actions were performed, by whom and when. After you have flagged vulnerabilities as ready for retesting on a project, you can request a round of retesting to be performed.
 Industry Standard Recommendations
Industry Standard Recommendations
 Mitigate Vulnerability
Mitigate Vulnerability
 Retest When Needed
Retest When Needed
 Timely Submission
Timely Submission
Address: 4th floor M- Arch Center,
Pashan-Sus Road, Baner, Pune 411021
Email: support@securityboat.net
Phone: +91 9175154999
Latest resources sent to your inbox weekly
Latest resources sent to your inbox weekly
Copyright @2025 SecurityBoat. All Rights Reserved by SecurityBoat.

Address: 4th floor M- Arch Center,
Pashan-Sus Road, Baner, Pune 411021
Email: support@securityboat.net
Phone: +91 9175154999
Latest resources sent to your inbox weekly
Latest resources sent to your inbox weekly
Copyright @2025 SecurityBoat. All Rights Reserved by SecurityBoat.

Address: 4th floor M- Arch Center,
Pashan-Sus Road, Baner, Pune 411021
Email: support@securityboat.net
Phone: +91 9175154999
Latest resources sent to your inbox weekly
Latest resources sent to your inbox weekly
Copyright @2025 SecurityBoat. All Rights Reserved by SecurityBoat.